Ready to see the market clearly?
Sign up now and make smarter trades today
Trading Basics
January 27, 2025
SHARE
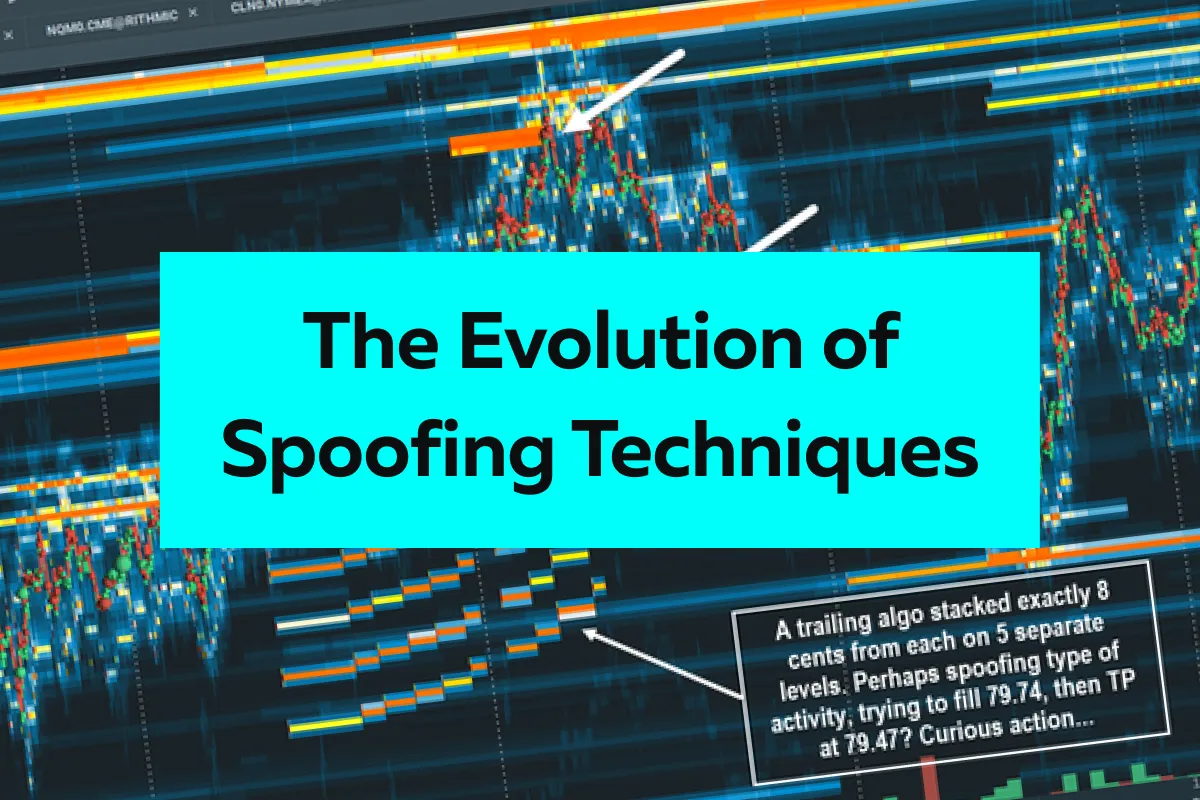
The Evolution of Spoofing Techniques in 2025: What to Watch For
You might be spotting trends. But a few are not! In the world of trading, some market participants play a different game. Generally, their game involves the following:
- Manipulation,
- False signals,
and
- Deceit.
The manipulative practice, known as spoofing, continues to be a headache despite ongoing regulatory efforts. As we move into 2025, these spoofing techniques are becoming more sophisticated. This makes it crucial for you to stay one step ahead. But are you ready?
In this article, we will study how spoofing in trading is evolving. We will specifically focus on the advanced spoofing tactics expected to emerge in the near future. You will learn how to spot spoofing activities and use our advanced trading tools like Bookmap to detect suspicious market behavior in real time.
We will also see how market manipulation detection and anti-spoofing technology are evolving. Read till the end to respond faster and protect yourself against the risks posed by spoofing. Let’s get started.
Regulatory Crackdowns and Technological Advancements in Detection
In recent years, there has been increased scrutiny of spoofing in trading. Several regulators like the SEC, CFTC, and their global counterparts are imposing hefty fines and penalties. Let’s talk about some recent examples:
| The case of BofA securities (2023) | The case of J.P. Morgan (2022) |
|
|
These enforcement actions clearly show the seriousness of combating fraudulent practices. Regulators and exchanges nowadays are even using advanced spoofing tactics that exploit market inefficiencies. To enhance market manipulation detection, they are turning to
- Artificial Intelligence (AI),
and
- Machine learning technologies.
These tools analyze trading patterns. This analysis helps them to detect anomalies, such as sudden order cancellations or irregular volumes. Additionally, regulators and exchanges also use anti-spoofing technologies. Check the graphic below to see how they help:
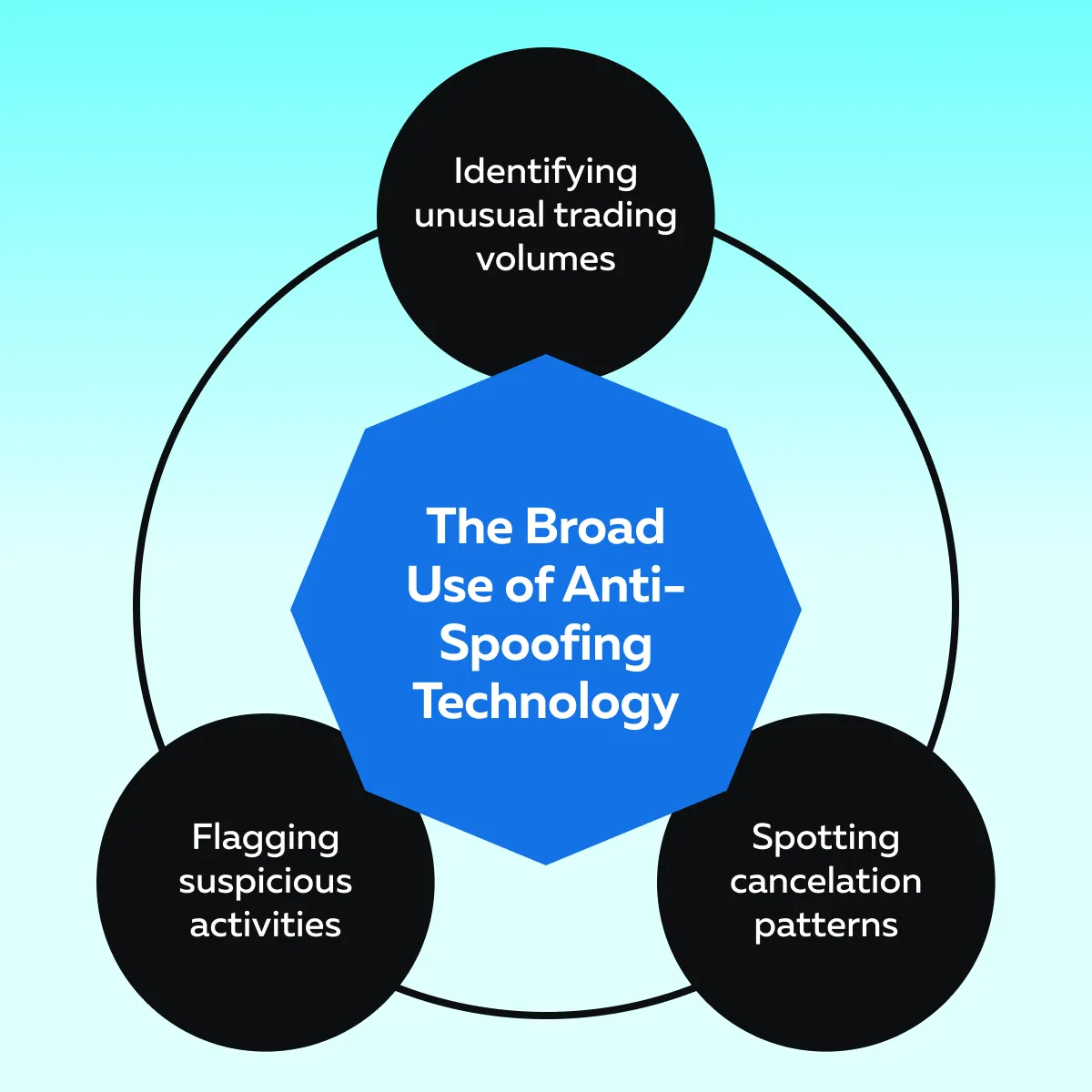
The ongoing adoption of spoofing techniques in 2025 and their integration with predictive analytics has helped to maintain market integrity.
Predicted Spoofing Tactics in 2025
As technology evolves, so do tactics. In 2025, we can expect to see more sophisticated spoofing techniques. They will be specifically designed to deceive both human traders and algorithms. These tactics will likely involve:
- Automation,
- AI-driven strategies,
and
- Cross-market manipulation.
These will make it harder to detect false signals. Let’s learn about some advanced spoofing tactics:
A) Sophisticated Layering Strategies
First of all, let’s understand what “layering” is. It is a tactic in which traders place multiple spoof orders. These orders are placed at different price levels. Such a placement creates a deceptive market signal. In this way, this strategy manipulates the market. It shows false demand or supply, luring other traders into unfavorable positions.
As technology evolves, advanced spoofing tactics are expected to become even more automated. This enables spoofers to execute layering across various instruments and markets simultaneously. Furthermore, by leveraging automation, future spoofing techniques in 2025 may evade traditional detection systems.
These tactics can deceive single-market algorithms by spreading spoof orders across related instruments, such as equity derivatives and commodities. Check the graphic below to see how to combat this:
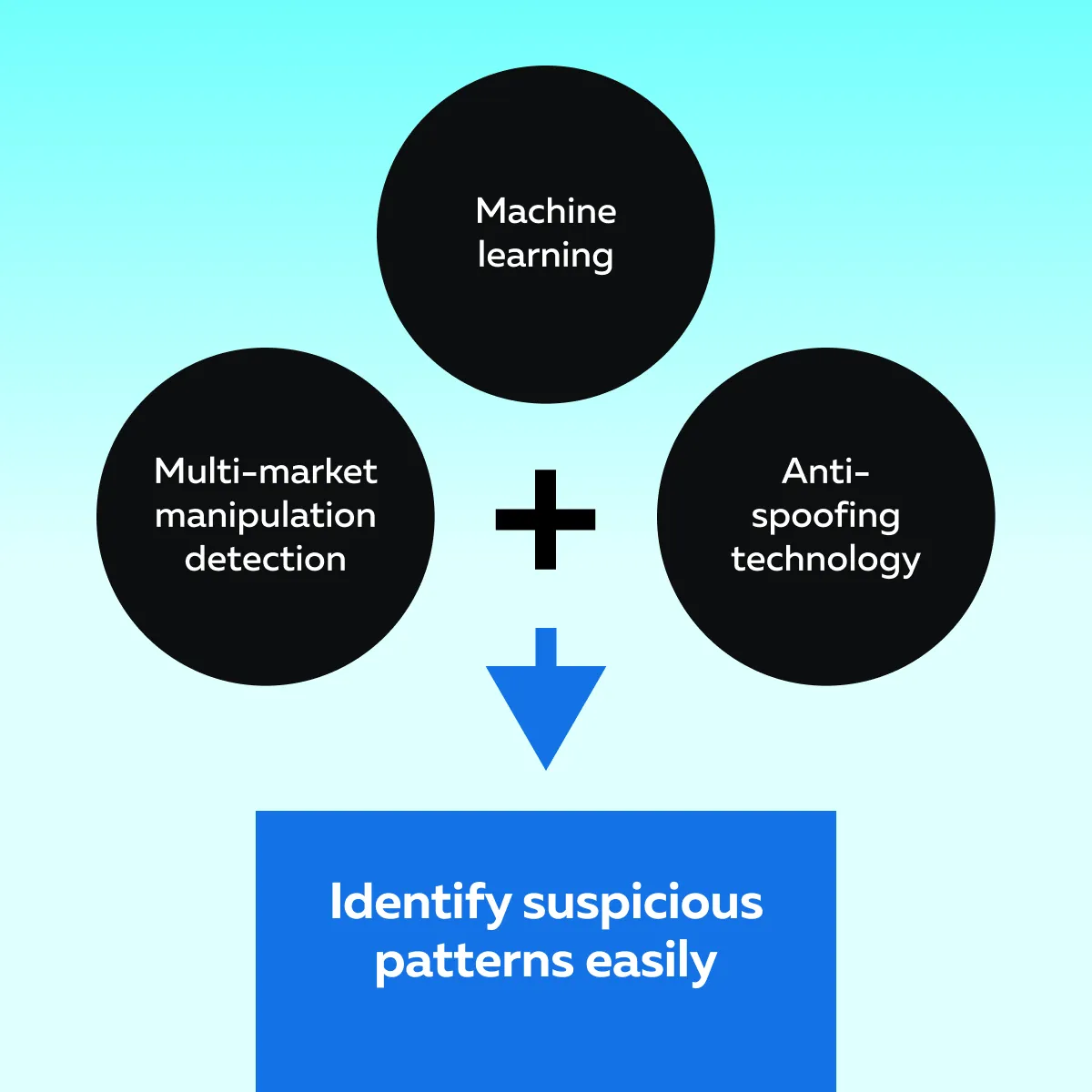
Additionally, real-time data analysis and predictive models will also play an important role. They will safeguard market integrity from these increasingly sophisticated threats.
B) Cross-Market Spoofing
In cross-market spoofing, traders manipulate related assets, such as equity futures and ETFs. By doing so, they mislead algorithms that monitor single-market trends. In this tactic, traders place deceptive orders in one market, such as S&P 500 futures. Through this, spoofers can indirectly influence the price movements of correlated assets like the SPY ETF.
These advanced spoofing tactics exploit the interconnectedness of markets. This even disrupts trading algorithms relying on “isolated trend analysis.” To counteract this, market manipulation detection must focus on:
- Cross-asset monitoring,
and
- The development of anti-spoofing technology that is capable of analyzing interdependent trading behaviors.
For more clarity, let’s see a cross-market spoofing example:
A spoofer manipulating S&P 500 futures can indirectly influence the price movements of the SPY ETF, which tracks the same index. By placing large spoof orders in the futures market, the spoofer creates an illusion of increased buying or selling pressure. This false signal impacts SPY ETF algorithms. As a result, it causes price shifts in both markets.
C) Time-Sensitive Spoofing
Time-sensitive spoofing targets moments of heightened volatility, such as during major news releases or economic announcements. Spoofers flood the market with orders just milliseconds before critical updates. By doing so, they try to exploit the delay in:
- Human reaction,
and
- Machine processing.
These spoofing techniques rely on high-speed execution and cancellation. This way, these tactics manipulate order books temporarily and create false market signals. By acting in these split-second windows, spoofers mislead both traders and algorithms.
Therefore, anti-spoofing technology must incorporate real-time surveillance and adaptive algorithms. These will detect and mitigate such rapid manipulative activities. Also, this ensures market stability even during volatile periods.
Now, for more clarity, let’s even see a time-sensitive spoofing example:
- Say a trader is using a predictive spoofing technique.
- They flood markets with fake orders.
- The orders are placed milliseconds before significant announcements, such as the Federal Reserve interest rate announcement.
- The spoofer places large buy orders on U.S. Treasury futures.
- These orders create an artificial perception of market demand.
- In this way, the trader exploits delays in both human decision-making and machine responses.
- Also, they mislead algorithms into upward price adjustments.
- Now, before the announcement’s actual impact unfolds, the spoofer cancels their orders.
- By doing so, the spoofer benefits from the brief price movement.
Please note that such tactics are particularly effective in high-volatility periods when trading systems are under stress. To counter these advanced spoofing tactics, traders will require anti-spoofing technology. Such a technology must be capable of:
- Real-time data analysis,
and
- Pattern recognition.
These capabilities can detect and nullify manipulative activities. Protect your trades by identifying spoofing activity before it impacts your strategy with Bookmap.
D) AI-Augmented Spoofing
It is worth mentioning that AI-augmented spoofing represents a significant leap in advanced spoofing tactics. In it, spoofers utilize artificial intelligence. They identify weaknesses in:
- Anti-spoofing technology,
and
- Market surveillance systems.
By analyzing trading data, AI algorithms detect patterns in enforcement gaps. They even spot inefficiencies in market manipulation detection.
Prediction for 2025
By 2025, spoofers may deploy AI-driven bots. These bots will be capable of precisely mimicking legitimate trading behaviors. Moreover, these bots can quickly adjust their actions to blend with market activities so that they can evade detection.
For example,
- An AI bot does not place and cancel large orders uniformly.
- The bot staggers the following:
- Timing,
- Volume,
and
- Market location.
- By doing so, they make it feel like all the trades are genuine.
- Such bots could even operate across multiple markets.
- They can exploit vulnerabilities and ensure their tactics are harder to trace.
To counteract these evolving spoofing techniques in 2025, market regulators and exchanges must enhance anti-spoofing technology with AI and machine learning.
Implications for Retail and Institutional Traders

Please note that evolving spoofing techniques in 2025 can significantly amplify short-term price volatility. This amplification can create both opportunities and risks for day traders and scalpers. Here are a few examples:
- Advanced spoofing in trading manipulates bid-ask spreads.
- It encourages traders to enter positions based on false signals.
- While this volatility creates profit opportunities, it also heightens the risk of losses when the market quickly corrects itself.
- Retail traders, especially those relying on rapid decision-making, are particularly vulnerable to these schemes.
Challenges for Algorithmic Systems
One must be aware that spoofing tactics target algorithmic systems. These tactics exploit the reliance of algorithmic systems on:
- Order flow,
and
- Market sentiment data.
For example, let’s assume an AI-powered trading bot might misinterpret spoof orders as genuine activity. This triggers erroneous trades that result in significant financial losses.
In this way, these advanced spoofing tactics not only mislead algorithms but also destabilize market dynamics. This makes it harder for retail and institutional traders alike to operate.
Importance of Institutional Detection Systems
To combat these threats, institutional traders must adopt anti-spoofing technology. Check the graphic below to see the essential capabilities that anti-spoofing technology must include:

For analysis purposes, traders can also use our advanced market analysis tool, Bookmap. With this tool, you can visualize liquidity. Such a visualization helps you to identify irregularities linked to spoofing, such as:
- Unusual order clustering,
or
- Abrupt cancellations.
Bookmap also enhances market manipulation detection. It allows you to get a clearer view of market conditions. For more clarity, let’s read an example and see how Bookmap’s liquidity tools detect spoofing:
-
- Say there is a trader named Sarah who uses Bookmap.
- She is responsible for managing large positions in the equity futures market.
- One day, while analyzing the S&P 500 futures market, she noticed an unusual pattern in her Bookmap liquidity tool.
- The market depth chart, which provides real-time data on the order book, begins to show large orders at specific price levels.
- She observes that a spoofer has placed 1,000 contracts at a certain price level in the S&P 500 futures market, only to cancel them milliseconds later.
- These orders rapidly appear and then disappear within seconds.
- Such large-order placement and rapid cancellation give a false impression of market interest.
- It is a classic indicator of spoofing in trading.
- By using Bookmap’s heatmap feature, Sarah easily spots this anomaly.
- The heatmap visually highlights these canceled orders.
- It even shows the density of market orders at each price level.
- The color-coded system on the heatmap allows her to see where the spoofed orders were placed, even after they’ve been canceled.
- She noticed that a large order cluster at 4,000 contracts appeared at a specific price level but vanished within seconds. (an obvious sign of manipulation).
Spot unusual market behavior with Bookmap’s advanced visualization tools, helping you avoid manipulation traps.
How Traders Can Stay Ahead of Spoofing Tactics?
To stay ahead of spoofing techniques in 2025, traders need powerful tools. Using them, they can:
- Monitor live order flow,
and
- Detect unusual market behavior.
Our platform, Bookmap, with its liquidity visualization tools, allows you to track real-time order book data. With these tools, you can spot suspicious large orders that are placed and canceled quickly. Bookmap’s heatmap and liquidity indicators highlight areas where orders appear and disappear rapidly. This gives you a visual representation of market depth.
This transparency helps to identify market manipulation detection patterns, such as clusters of orders that seem inconsistent with:
- Actual trade volume,
or
- Price movements.
When such anomalies are detected, traders can prevent losses caused by false market signals. Use Bookmap to track real-time order flow and detect spoofing patterns before they affect your trades.
How to Spot Inconsistencies Between Executed Trades and Visible Orders?
To avoid falling victim to spoofing techniques in 2025, traders should remain vigilant about inconsistencies between:
- Executed trades,
and
- Visible orders in the order book.
A hallmark of spoofing in trading is when large orders are placed but are not executed. They are canceled before any trade is made. Be aware that these orders are only designed to mislead market participants into thinking there is greater market interest at a particular price level. Check the graphic below to learn how you can avoid such a situation.
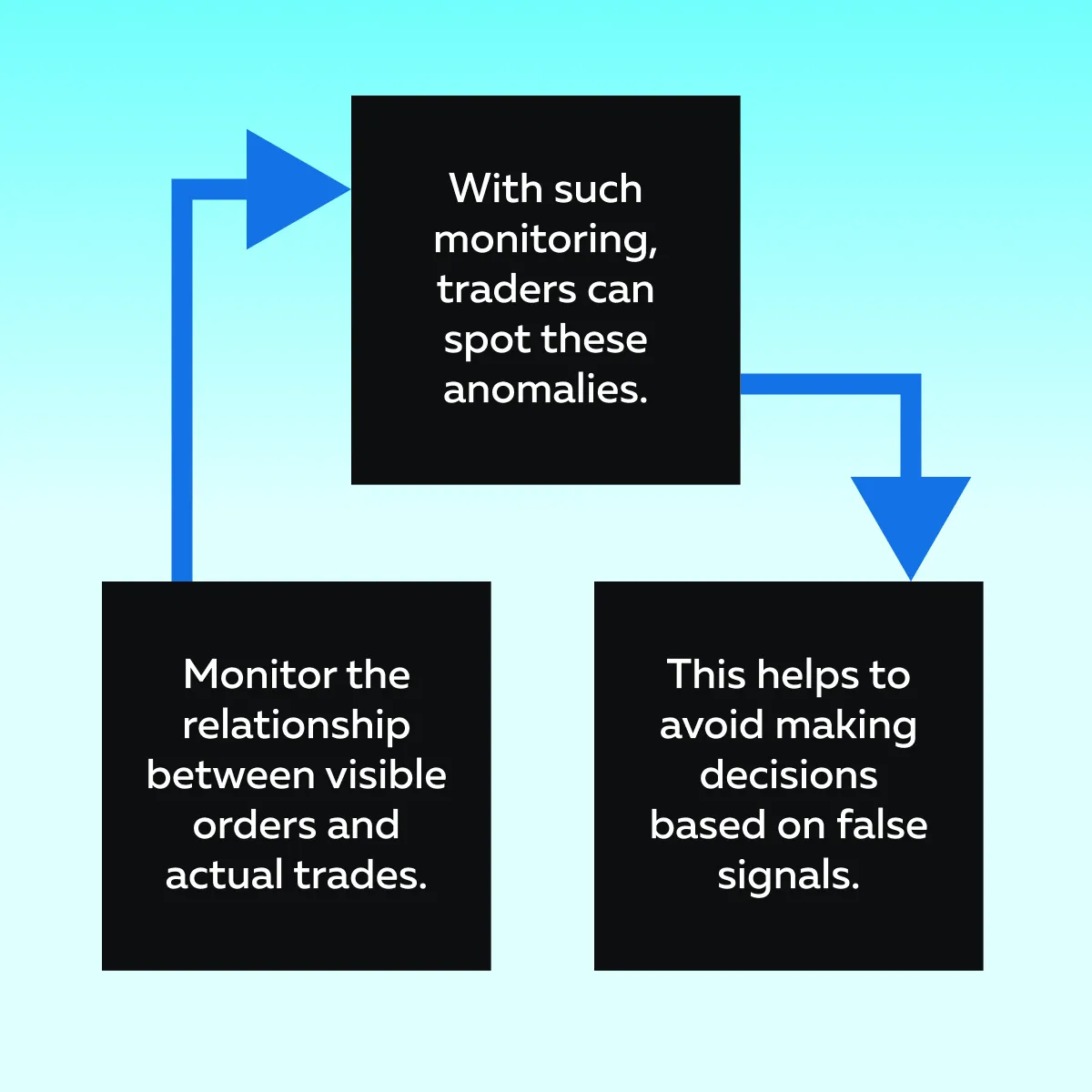
To achieve this, use our advanced market analysis tool, Bookmap. It helps you identify these discrepancies by displaying order book depth in real time. With Bookmap, you can spot large and canceled orders quickly.
Stay Informed About Evolving Spoofing Tactics
Market manipulation is constantly evolving and advanced spoofing tactics are becoming more sophisticated every day. Therefore, traders must actively stay informed about these developments. Learn how to do so in the graphic below:

These sources will provide you with the knowledge necessary to recognize new spoofing methods. You can then adjust your strategies accordingly.
Conclusion
Despite significant regulatory efforts and advancements in anti-spoofing technology, spoofing remains a persistent issue in financial markets. Authorities like the SEC and CFTC have implemented fines and regulations to combat market manipulation. Despite that, spoofers continue to develop more sophisticated tactics to evade detection.
By using tools like Bookmap’s real-time liquidity visualization, you can easily detect suspicious market activity linked to spoofing. With Bookmap, you can monitor order flow and identify large orders that disappear without execution. In this way, you can spot manipulative patterns early. Use Bookmap’s real-time order flow tools to stay ahead of evolving spoofing tactics in 2025.